
Image credits: TechCrunch/Bryce Durbin
One cryptocurrency wallet maker claimed this week that hackers may be targeting people with an iMessage “zero-day” exploit, but all signs point to an exaggerated threat, if not an outright scam. Showing.
Trust Wallet’s official X (formerly Twitter) account I have written “We have received reliable information about a high-risk zero-day exploit targeting iMessage on the dark web, which can compromise your iPhone without even clicking a link. High-value target may be present. Each use increases the risk of detection.
The wallet maker recommended that iPhone users turn off iMessage completely “until Apple patches this,” even though there is no evidence that “this” exists.
The tweet went viral and had been viewed more than 3.6 million times as of publication.The wallet was trusted after a few hours as the post received attention I wrote a follow-up post. The wallet maker emphasized its decision to go public, saying it will “proactively communicate potential threats and risks to the community.”
Trust Wallet did not respond to TechCrunch's request for comment. Apple spokesman Scott Radcliffe declined to comment Tuesday.
As it turns out, According to Éowyn Cheng, CEO of Trust Wallet:, “Intel” is an ad on a dark web site called CodeBreach Lab where someone is offering the alleged exploit described above for $2 million in Bitcoin cryptocurrency. The ad, titled “iMessage Exploit,” states that the vulnerability is a remote code execution (or RCE) exploit that requires no interaction from the target (commonly known as a “zero-click” exploit) and is available in the latest versions of iOS. claims to work. Some bugs are called zero-day because the vendor hasn't had time to fix the vulnerability or they are zero-day. In this case, there is no evidence of an exploit to begin with.
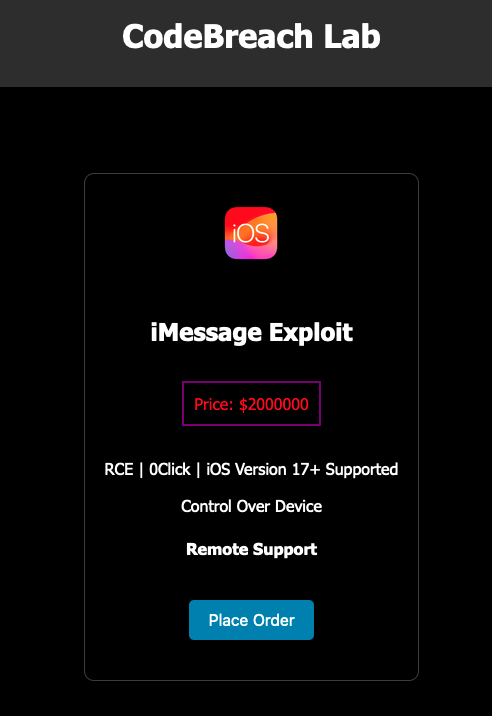
Screenshot of a dark web ad claiming to sell a suspected iMessage exploit. Image credit: TechCrunch
RCE is one of the most powerful exploits because it allows hackers to remotely control the target device over the Internet. Exploits like his RCE, combined with zero-click functionality, are extremely valuable as they allow attacks to be carried out invisibly without the device owner knowing. In fact, companies that acquire and resell zero-days are currently offering anywhere from $3 million to $5 million for that kind of zero-click zero-day. This shows how difficult it is to find and develop this type of exploit.
inquiry
Do you have any information about actual zero-days? Or about spyware providers? Securely from a non-work device, on Signal (+1 917 257 1382), or on Telegram, Keybase and Wire @lorenzofb, or email Lorenzo Franceschi-Bicchierai You can contact. You can also contact TechCrunch via SecureDrop.
Given the context of how and where this zero-day is being sold, this is all just a scam, and Trust Wallet has fallen for it, creating what those in the cybersecurity industry call FUD, or “uncertainty and It is very likely that they spread fear. Doubt. “
Zero-days exist and have been used by government hacking forces for years. But in reality, unless you're a high-risk user, such as a journalist or dissident in an oppressive regime, you probably don't need to turn off iMessage.
Lockdown mode is a special mode that disables certain Apple device features, with the goal of reducing the ways hackers can attack your iPhone or Mac.
Apple says there is no evidence that anyone has hacked someone else's Apple device while in lockdown mode. Some cybersecurity experts say: Luna Sandvik And that researcher The folks at Citizen Lab, which has investigated dozens of iPhone hacks, recommend using lockdown mode.
CodeBreach Lab itself appears to be a new, unproven website. When we checked, Google only returned 7 results. One of his posts was on a popular hacking forum asking people if they had heard of CodeBreach Lab.
CodeBreach Lab claims on its home page (albeit with a typo) that it offers several other exploits beyond iMessage, but provides no further evidence.
The owners describe CodeBreach Lab as a “cyberdisruption nexus.” But perhaps it would be more appropriate to call it a marriage of bragging and naivety.
TechCrunch was unable to reach CodeBreach Lab for comment because it does not have a way to contact the alleged suspect companies. When we tried to purchase the alleged exploit, the website asked for the buyer's name and email address and sent $2 million in Bitcoin to a specific wallet address on a public blockchain. I asked him to send me the money. From what we've checked, no one has ever done that before.
In other words, if someone wanted this purported zero-day, they would have to transfer $2 million to a wallet, but there is currently no way to know who the wallet belongs to or even contact them.
And it is very likely that this will continue.


