Quantum computing is a revolutionary force that has the potential to redefine industries, including the cryptocurrency market. As a result, Bitcoin, the largest cryptocurrency with a market capitalization of $1.27 trillion, is at a crossroads.
Bitcoin faces significant vulnerabilities to quantum computing because it relies on the Proof-of-Work (POW) consensus protocol and Elliptic Curve Cryptography (ECC) for encryption.
Quantum computing threatens Bitcoin
The POW mechanism, which is essential to the operation of Bitcoin, involves miners solving complex mathematical problems to verify transactions and secure the network. But quantum computing's ability to perform calculations at unprecedented speeds threatens to upset this balance.
Quantum algorithms like Grover's could theoretically solve these problems much faster than classical computers. Therefore, this technology could centralize mining power and undermine the decentralized spirit of Bitcoin.
“Using the latest values for quantum computing technology, the Bitcoin network hashrate will increase at the same rate over time according to Moore's Law, and the estimated time period until a single quantum computer completely outperforms is approximately It's been 27 years. By mining the rest of the network, we can take over complete control of it,” wrote University of Kent faculty member Dan A. Byrd.
Additionally, Bitcoin's essential ECC encryption, which protects wallet addresses, is also at risk. Quantum computers could one day use Scholl's algorithm to defeat his ECC, exposing Bitcoin transactions to potential security breaches.
This vulnerability specifically extends to legacy addresses that contain a significant portion of Bitcoin founder Satoshi Nakamoto's holdings.
“Once the public key is known, an ECDSA-adapted Scholl algorithm can be run on an ideal quantum computer to find the public key in polynomial time. Classically, finding a solution takes “It is polynomial and takes orders of magnitude more time… It is speculated that polynomial time is potentially feasible and that eventually ECDSA will be decipherable by quantum computers,” Acheron Trading researchers wrote. Masu.
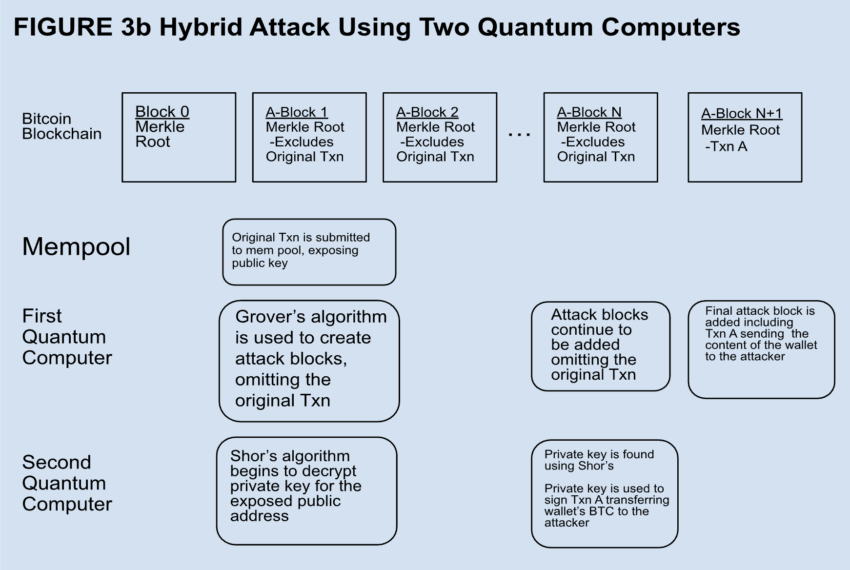
Despite these challenges, the immediate threat remains theoretical. Current quantum computing power is far beyond what is needed to thwart Bitcoin mining or effectively break ECC encryption, as demonstrated by the largest Grover search to date using 6 qubits. It's far from scale. But quantum advantage, a state in which quantum computers will outperform traditional computers at certain tasks, is on the horizon.
It seems unlikely that the Bitcoin community will move away from POW to alternative consensus mechanisms such as Proof of Stake (POS). Even cryptologist Adam Back says that PoS cryptocurrencies lack immutability, decentralization, and verifiable significant production costs, highlighting their fundamental differences from Bitcoin.
“It's hard money, immutable, decentralized, and verifiably expensive to produce. The technology is structured to be economically stable and difficult to change in practice. PoS Coins don't have those characteristics. They have CEOs, and they have dozens of competitors. There's only one Bitcoin,” Buck argued.
This resistance to change reflects the importance of proactive measures to protect networks from future quantum threats.
Read more: Proof of Work and Proof of Stake Explained
The path forward requires a delicate balance between preserving Bitcoin's fundamental principles and adapting to technologies such as quantum computing. Upgrading encryption methods and exploring quantum-resistant algorithms are important steps to ensure Bitcoin's resilience. The transition to secure quantum cryptography protects against immediate threats and secures networks against future advances in quantum computing.
Disclaimer
In accordance with Trust Project guidelines, BeInCrypto is committed to fair and transparent reporting. This news article is intended to provide accurate and timely information. However, before making any decisions based on this content, readers are encouraged to independently verify their facts and consult a professional. Please note that our Terms of Use, Privacy Policy, and Disclaimer have been updated.


