
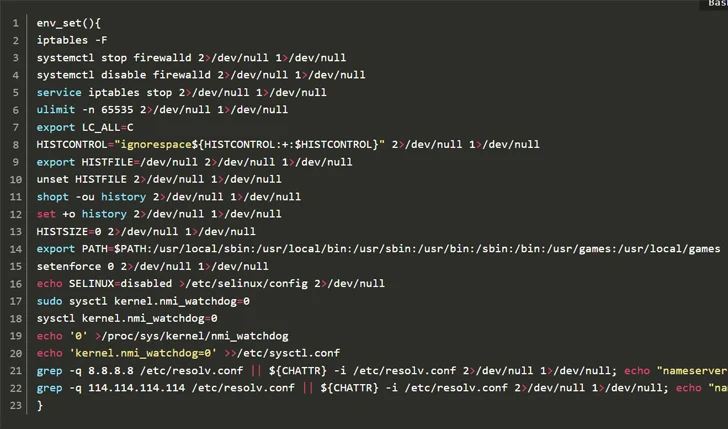
Threat actors are targeting Apache Hadoop YARN, Docker, Atlassian Confluence, and Redis services as part of a new malware campaign aimed at delivering cryptocurrency miners and generating reverse shells for persistent remote access. It targets vulnerable, misconfigured servers that run.
“Those tools allow attackers to issue exploit code, exploit common misconfigurations to exploit N-day vulnerabilities, and enable remote code execution (RCE),” said Matt Muir, a security researcher at Cado. ) attacks and infect new hosts.” Hacker News.
This activity is codenamed spin a thread This is from a cloud security company and overlaps with cloud attacks by TeamTNT, WatchDog, and a cluster called Kiss-a-dog.
It all starts by deploying four new Golang payloads that can automate the identification and exploitation of susceptible Confluence, Docker, Hadoop YARN, and Redis hosts. Spreader utilities utilize masscan or pnscan to locate these services.

“In the case of a Docker compromise, the attacker spawns a container and escapes from there to the underlying host,” Muir explained.
The initial access then installs rootkits such as libprocesshider and diamorphine to hide malicious processes, drops the Platypus open source reverse shell utility, and ultimately installs additional tools to launch the XMRig miner. This will pave the way for expansion.
“Attackers spend significant time understanding the types of web-enabled services deployed in cloud environments, stay on top of reported vulnerabilities in those services, and use that knowledge to target “It is clear that we are gaining a foothold in the environment,” the company said.
This development comes as part of a series of attacks targeting cloud infrastructure starting in May 2023, when the 8220 Gang attacked Apache Log4j (CVE-2021-44228) and Atlassian Confluence Servers and Data Centers (CVE-2022-26134). This comes after Uptycs revealed that it was exploiting a known security flaw in . Until February 2024.
Security researchers Tejaswini Sandapola and Shilpesh Trivedi said, “By leveraging internet scanning for vulnerable applications, the group is able to identify potential points of entry into cloud systems and identify unpatched systems. They are exploiting vulnerabilities to gain unauthorized access.”
“Once infiltrated, they deploy a series of sophisticated evasion techniques and demonstrate a deep understanding of how to navigate and manipulate cloud environments, including disabling security enforcement and changing firewall rules. changes, and removal of cloud security services to ensure malicious activity remains undetected.”
Targeting both Windows and Linux hosts, the attack aims to deploy cryptocurrency miners, but before doing so it takes a series of steps that prioritize stealth and evasiveness.

Additionally, cloud services, primarily for artificial intelligence (AI) solutions, continue to be exploited to drop cryptocurrency miners and host malware.
“Mining and AI both require access to large amounts of GPU processing power, so there is potential for some migration to base hardware environments,” HiddenLayer noted last year.
Cado, in its H2 2023 Cloud Threat Research Findings report, found that attackers are increasingly targeting cloud services that require specialized technical knowledge to exploit, and cryptojacking is no longer the only motive. It points out that it is not.
“The discovery of new Linux variants of the ransomware family, including Abyss Locker, shows an alarming trend of ransomware on Linux and ESXi systems,” the company said. “Cloud and Linux infrastructures are now exposed to a wider variety of attacks.”


